CAT.NET Microsoft’s Code Analysis Tool
Microsoft has introduced a new code analysis tool called CAT.NET to help analyze source code for security flaws within managed applications. This is a visual studio add-in that works directly within Visual Studio, so there is no need for separate programs. The tool will trace through all statements, methods, and assemblies referenced within the application. It is currently on Version One in CTP. Its rules look to identify the following flaws:
- Cross Site Scripting (XSS)
- SQL Injection
- Process Command Injection
- File Canonicalization
- Exception Information (a form of Information Leakage)
- LDAP Injection
- XPATH Injection
- Redirection to User Controlled Site
I executed the tool against a web application with the following code snippet:

The results of the scan are provided below:
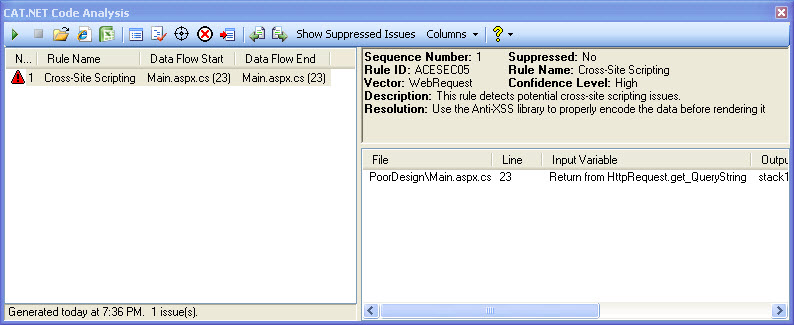
As you can see from the above samples, the tool does a good job of distinguishing between threats. By default, asp:textbox will encode its text value, whereas the label control will not. The information provided by the tool is very helpful as well. It shows what file and what line of code is the offender. It also recommends a resolution to help protect against this. For developers new to focusing on security, it would be nice if the tool gave the link to the Anti-XSS library or a sample code snippet to show how to implement the fix. That information is pretty easy to find and for a free tool it provides some good general protection for your code.
The tool can be downloaded at http://www.microsoft.com/downloads/details.aspx?FamilyId=0178e2ef-9da8-445e-9348-c93f24cc9f9d&displaylang=en.
I have tried this tool on a few different projects and it has worked pretty well. I have found that on very large solutions I ran into out of memory exceptions. This is a limitation for all add-ins because Visual Studio is limited to 2GB of space. The larger projects use up more of that so the tool doesn’t have space to function properly. This can be managed by selecting specific projects to analyze.



